Importing Certificates into Trusted Root CA Certificate Store
The device provides its own Trusted Root Certificate Authority (CA) Certificate store. This lets you manage certificate trust. Depending on certificate size, you can import up to approximately 150 certificates into the Trusted Root CA Certificate per TLS Context.
Instead of importing CA certificates into the Trusted Root CA Certificate store for a TLS Context, you can enable the TLS Context to use the device's default list of CAs. To do this, configure the 'Use default CA Bundle' parameter to Enable in the TLS Contexts table (see Configuring TLS Certificate Contexts). To view the default CAs, see Viewing Default Certificate Authorities.
For TLS Contexts that you have enabled the use of the device's default CAs:
|
●
|
The default CAs are not listed in the Trusted Root CA Certificate store of these TLS Contexts (even though they are used). |
|
●
|
You can only enable the use of the default CAs for TLS Context IDs 0 through 4. |
|
●
|
In addition to using the default CAs, you can import other CAs into the Trusted Root CA Certificate store. In this setup, the device uses both the default CAs and the ones that you have imported. |
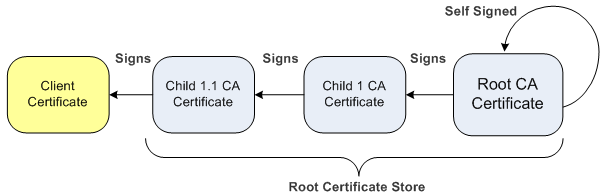
The Trusted Root CA Certificate store can also be used for certificate chains. A certificate chain is a sequence of certificates where each certificate in the chain is signed by the subsequent certificate. The last certificate in the list of certificates is the Root CA certificate, which is self-signed. The purpose of a certificate chain is to establish a chain of trust from a child certificate to the trusted root CA certificate. The CA vouches for the identity of the child certificate by signing it. A client certificate is considered trusted if one of the CA certificates up the certificate chain is found in the server certificate directory. For the device to trust a whole chain of certificates per TLS Context, you need to import them into the device's Trusted Root CA Certificate, as described below.
You can also import multiple TLS root certificates in bulk from a single file. Each certificate in the file must be Base64 encoded (PEM). When copying-and-pasting the certificates into the file, each Base64 ASCII encoded certificate string must be enclosed between "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----".
You can import only Base64 (PEM) encoded X.509 certificates into the Trusted Root CA Certificate store.
|
➢
|
To import certificates into Trusted Root CA Certificate store: |
|
2.
|
Select the required TLS Context, and then click the Trusted Root Certificates link located below the table; the Trusted Certificates table appears. |
|
3.
|
Click the Import button, and then select the certificate file: |
|
4.
|
Click OK; the certificate is imported into the Trusted Root CA Certificate store: |
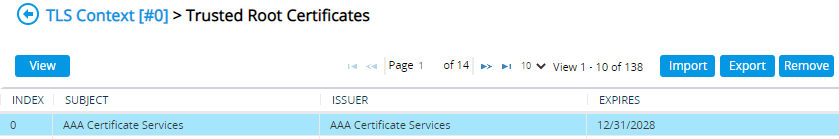
In addition to the Import button, the Trusted Root CA Certificate store provides the following buttons:
|
■
|
Remove: Deletes the selected certificate. |
|
■
|
Export: Downloads the selected certificate to your compuuter. |

